Analysing what a phishing link might lead to
The Attempt
I received a message (SMS) from the German Minister of Finance telling me I was to receive 529.29 Euro. To claim that money, I just had to follow a link included in that message (original content in German, link disarming mine):
[Bundesminister für Finanzen]
Lieber Bürger Ihnen steht
noch ein ausstehender
betrag von 529.28 EUR zur
Verfügung. Clicken Sie hier:
https://itsssl[.]com/7sXQm
Apart from the obligatory spelling and grammar mistakes, this one does not even try to make an serious effort. Anyway. We'll do a short analysis to see what this thing's up to.
Gathering information
Letting aside the fact that I'd considering it highly unlikely that the Minister of Finance would be contacting me via SMS, the first thing appearing suspicous is the included URL. So let's have a look at that first.
For starters we'd like to know who own the domain. A whois lookup (e.g. via https://whois.com/whois) returns a US company "Jewella Privacy" in Harahan, Louisiana near New Orleans as registrant. The registered address shows to be a small diner called "Caffé Latte Da". At first sight, this does not seem to have much to do with the German Ministry of Finanace.
A web search for "Jewella Privacy" brings up https://jewellaprivacy.com/, which identifies it us a company providing "privacy services" to domain name registrants, so this is obviously leading nowhere.
Resolving the hostname via DNS returns two IP addresses. ipinfo.io tells us that both belong to Cloudflare, so this doesn't help either.
While we are sufficiently certain that we have not an legit notification from an official governmental institution here, we now surely want to learn more. Let's see this thing in action.
Going Live
browserling allows to test websites online in a sandboxed browser. While this is generally a paid service, the free but limited option is sufficient for occasional analysis.
Testing the URL in a simulated Chrome browser brings us to a site claiming to be owned by "Bundesministerium der Finanzen" (German Ministry of Finance). The URL visible in the address bar, however, can be seen as nabbsbs82g[.]temp[.]swtest[.]ru/de/de/index.php. The page states, again, that there is 529.28 Euro for me to collect. For good measure, it states that the form will only be valid for 24 hours, to put some further pressure on the targeted victim.
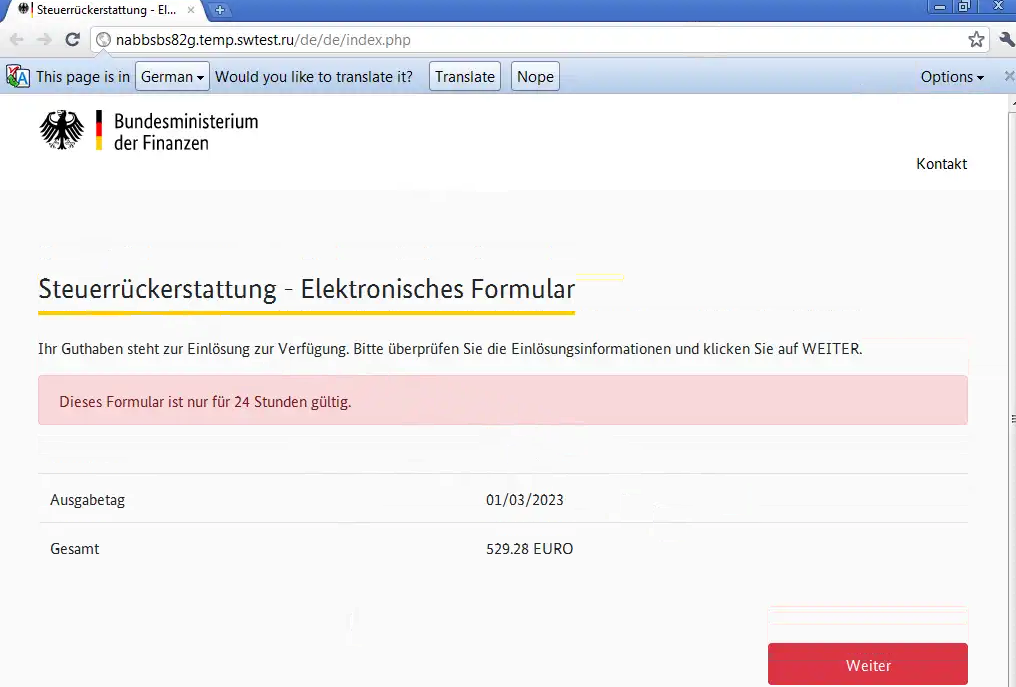
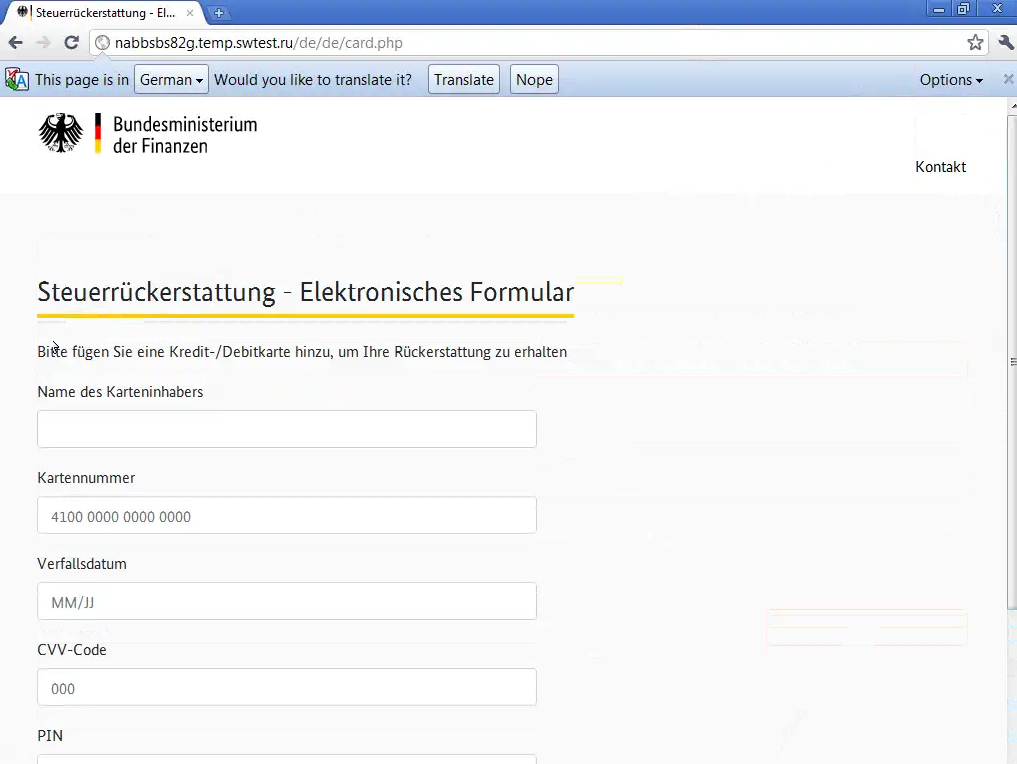
Clicking the button to proceed leads to nabbsbs82g[.]temp[.]swtest[.]ru/de/de/card.php, which reveals the true purpose of all of this. The site is asking for my credit card information in order to provide me with my money. For the sake of simplicity, I am expected to give my PIN as well.
Interestingly enough, not every attempt to run this in a sandbox leads to the fake ministry site trying to rob me for my credit card info. Sometimes accessing the URL simply leads to the genuine website of the German Ministry of Finance. This might indicate that some form of sandbox detection or something similar is at work here, which tries to evade detection of the fraudulent site by simply skipping it.